Overview
- This comprehensive guide on cybersecurity in healthcare covers preventive measures, incident response strategies, and recovery procedures to safeguard patient data and maintain operational continuity in the face of cyberattacks.
- It emphasizes the importance of implementing robust access controls, vulnerability assessments, monitoring, and backup systems, as well as adhering to frameworks like HIPAA and NIST Cybersecurity Framework to enhance cybersecurity posture.
- The guide highlights the necessity of creating an incident response plan and a crisis management plan, which outline steps for identifying, containing, and eradicating threats, as well as effectively communicating with stakeholders and mitigating reputational and legal consequences.
The recent cyberattack on Change Healthcare, a major player in the United States healthcare system, has sent shockwaves through the industry. This healthcare cyberattack, disrupting patient care and highlighting vulnerabilities in healthcare data security, serves as a stark reminder of the ever-present threat of cybercrime.
Medical practices hold a wealth of sensitive patient information, which makes them prime targets for cybercriminals. A successful healthcare cybersecurity breach can disrupt operations, compromise patient data, and erode trust. This guide equips healthcare providers with the best knowledge and tools to navigate the complex world of cybersecurity.
We'll walk you through:
- Preventative measures to stop cyberattacks in their tracks
- Effective response strategies to minimize damage during an incident
- Efficient recovery procedures to get your practice back on track
By following these steps, you can significantly improve your cybersecurity posture and ultimately safeguard patient care.
Let’s first look at the Change Healthcare cyberattack in detail for some context.
What is the Change Healthcare cyberattack?
Change Healthcare, a subsidiary responsible for managing patient records, revenue cycles, and prescriptions for Optum, fell victim to a ransomware assault orchestrated by Alphv/BlackCat.
In response, UnitedHealth Group (UHG), the parent company of Optum, swiftly disconnected Change Healthcare to contain the breach.
“The repercussions of this shutdown are estimated to be disrupting over $100 million in daily provider reimbursement.”
The repercussions of this shutdown are estimated to be disrupting over $100 million in daily provider reimbursement, potentially leading to various provider-related ramifications, such as:
- Issues filling prescriptions
- Unprocessed claims
- Missing ERA
- Delayed provider reimbursement
- Potential timely filing issues for impacted claims
- Failed eligibility transactions
How do cyberattacks impact healthcare?
The recent attack on Change Healthcare serves as a stark reminder that cyberattacks pose significant threats beyond the general disruption they cause.
Healthcare providers are entrusted with a vast amount of electronic protected health information (ePHI). This sensitive data comprises a patient's entire medical history, diagnoses, and even financial details.
Healthcare records continue to be one of the most lucrative items on the underground market, ranging from $250 to $1,000 compared to other items like credit cards only selling for an average of $100. This demonstrates the value of data like ePHI to cyber-attackers and their motivation for attacking healthcare institutions.
If ePHI is compromised, this information can have devastating consequences for patients. Potential implications can be identity theft, misuse of medical information, and even threats to their wellbeing.
Beyond the direct impact on patients, a successful cyberattack can cripple the operations of a healthcare facility; compromising the critical systems that healthcare facilities rely on to:
- Schedule appointments: Disrupted systems could prevent patients from booking necessary consultations or procedures.
- Maintain patient records: Compromised access could hinder the ability to accurately track medical history, potentially delaying diagnoses and treatment.
- Process prescriptions: Cyberattacks could disrupt the ability to dispense medication, leaving patients without access to vital treatments.
The financial repercussions of a cyberattack can also be significant. Healthcare providers face the risk of hefty fines for HIPAA violations around safeguarding patient data. Furthermore, they may be subject to lawsuits filed by affected patients seeking compensation for damages caused by the data breach.
“Perhaps the most damaging consequence of a cyberattack is the erosion of trust in a healthcare provider.”
Perhaps the most damaging consequence of a cyberattack is the erosion of trust in a healthcare provider. Public exposure of a data breach can severely tarnish a facility's reputation, leading to patient loss and negatively impacting future operations.
What does HIPAA say about cybersecurity?
The HIPAA Security Rule requires HIPAA covered entities and business associates (“regulated entities”) to implement authentication procedures “to verify that a person or entity seeking access to electronic protected health information is the one claimed.”
Healthcare providers (regulated entities) need to carefully choose how people access their systems based on an assessment of their specific risks. This ensures that private medical information (like test results and medications) stays protected.
Even though keeping this information confidential, accurate, and readily available is crucial, some healthcare providers still haven't put in place the necessary security checks as required by the Security Rule. This leaves them exposed to cyberattacks and data breaches and puts their patients' information at risk.
The HHS Office for Civil Rights (OCR) recently announced a resolution agreement with Banner Health to resolve issues of potential HIPAA non-compliance, including “failure to implement an authentication process to safeguard its electronic protected health information.” This incident included payment of $1.25M and implementation of a corrective action plan to be monitored by OCR for two years.
What is the biggest cyberattack in healthcare?
In September 2011, a reported 5 million patients were impacted by a significant data breach following the theft of backup tapes of electronic health records from Tricare.
Tricare is a healthcare program servicing active-duty troops, their dependents, and military retirees. The backups were stolen from the car of an individual responsible for transporting the tapes between facilities. Data compromised included Social Security numbers, names, addresses, personal health data, clinical notes, and phone numbers.
“One of the biggest cybersecurity threats facing physicians today is double extortion ransomware attacks.”
UCLA also suffered a data breach that is believed to have started in October 2014, but this activity did not appear to have malicious potential. But in May of 2015, a cyberattack involving the compromise of sensitive patient information was confirmed.
UCLA health received a $7.5 million fine for its failure to report the breach in a timely manner, which is a violation of the breach notification protocol specified under HIPAA.
Fast forward to 2024, and one of the biggest cybersecurity threats facing physicians today is double extortion ransomware attacks. Modern ransomware groups don't just encrypt data — they also exfiltrate sensitive records to extort even higher payments by threatening to leak the data publicly, violating regulations like HIPAA.
Despite reportedly paying $22 million to the Alphv/BlackCat ransomware gang, Change Healthcare finds itself remaining in a vulnerable position. Despite the massive payment, an affiliate of Alphv/BlackCat claims Alphv/BlackCat kept the full ransom while still retaining possession of over 4TB of stolen data from insurance companies and pharmacies.
Most common healthcare cyberattacks
Healthcare practices face a constant threat of cyberattacks.
These malicious attempts aim to steal valuable patient data, disrupt critical operations, and extort money. Recognizing the different types of attacks allows healthcare providers to implement effective prevention strategies.
Here's a breakdown of the most common healthcare cyberattacks with real-world examples:
Phishing attacks
Deceptive emails that often appear to come from legitimate sources like colleagues, patients, or even healthcare institutions. They may contain urgent requests or enticing offers, tricking recipients into clicking malicious links or downloading attachments that infect devices with malware:
- Colleagues: A phishing email might appear to be from a coworker requesting access to patient records or urging the recipient to click on a link to download a shared file (containing malware).
- Patients: Malicious actors might send emails disguised as patients seeking urgent medical attention or appointment confirmations. This approach tricks staff into clicking on infected links.
- Healthcare institutions: Phishing attempts could mimic official emails from healthcare organizations, urging recipients to update their login credentials on a fake website designed to steal sensitive information.
Data breaches
Unauthorized individuals gain access to protected patient information. Data breaches can happen through various means — including hacking into computer systems, exploiting software vulnerabilities, or even physical theft of devices containing sensitive data:
- Unsecured mobile devices: A healthcare worker might lose their smartphone or tablet containing unencrypted patient data. This physical breach could expose a large amount of sensitive information if proper safeguards are not in place.
Malware
This malicious software can take many forms, including viruses, spyware, and ransomware. Malware can steal sensitive patient data, disrupt operations, and even hold systems hostage for ransom payments:
- Ransomware: A ransomware attack could encrypt a hospital's electronic health records (EHR) system, rendering them inaccessible. The attackers might then demand a hefty ransom payment to decrypt the data, potentially crippling patient care and causing significant financial losses.
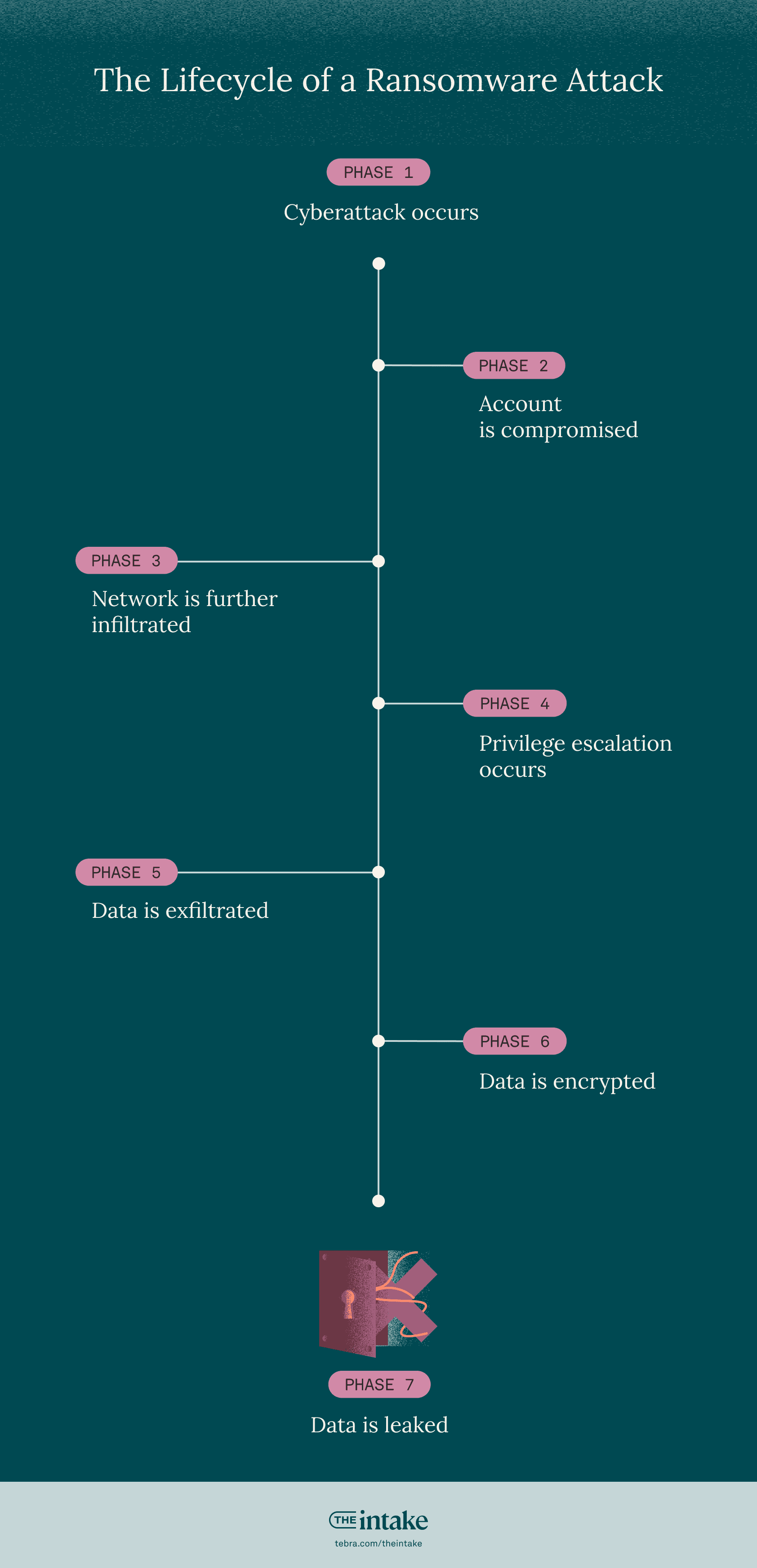
What does a ransomware attack look like?
The following is what a ransomware attack looks like in reality:
1. Cyberattack occurs: For instance, a cybercriminal sends a deceptive email posing as a legitimate source (colleague, patient, healthcare institution) to an employee. This email tricks the recipient into clicking a malicious link or downloading an attachment containing malware.
2. Account is compromised: Unaware of the deception, the employee falls victim to the phishing attempt and enters their login credentials on a fake website designed to steal them. This grants unauthorized access to the employee's account.
3. Network is further infiltrated: Leveraging the compromised employee account, the attacker can infiltrate the healthcare network. They then begin exploring and navigating through different systems, searching for accounts with higher privileges.
4. Privilege escalation occurs: The attacker actively seeks administrative or privileged accounts within the network. These accounts grant broader access to sensitive data and systems.
“In some cases, the attacker may deploy malware that encrypts critical systems, rendering them unusable.”
5. Data is exfiltrated: Once the attacker acquires privileged credentials, they exploit them to access confidential patient information. This data could include medical records, financial details, or other sensitive information.
6. Data is encrypted: In some cases, the attacker may deploy malware that encrypts critical systems, rendering them unusable. This often comes with a ransom demand, forcing the healthcare organization to pay to regain access to their data.
7. Data is leaked: As a pressure tactic to extort money, the attacker might selectively leak stolen patient data online if the ransom demands aren't met. This further emphasizes the urgency for the victim to comply.
Healthcare cyberattack prevention checklist
Now that we've established the critical role of cybersecurity in healthcare and the potential consequences of cyberattacks, let's go into the actionable steps to take.
This cyberattack prevention checklist outlines essential measures to significantly reduce the risk of a successful attack.
| Access controls and authentication: Dos | Access controls and authentication: Don’ts |
| Implement strong password policies: Enforce complex passwords and require regular password changes. | Reuse of passwords across accounts: Password Managers prevent this. |
| Limit telemedicine use to approved devices. | Rely solely on passwords for user authentication. |
| Consider passwordless authentication like biometrics or security keys where possible. | Grant widespread access to sensitive data without proper justification. |
| Manage account provisioning/deprovisioning to remove old user access promptly. | |
| Mandate use of enterprise password manager tools to generate, store and rotate unique, complex credentials. |

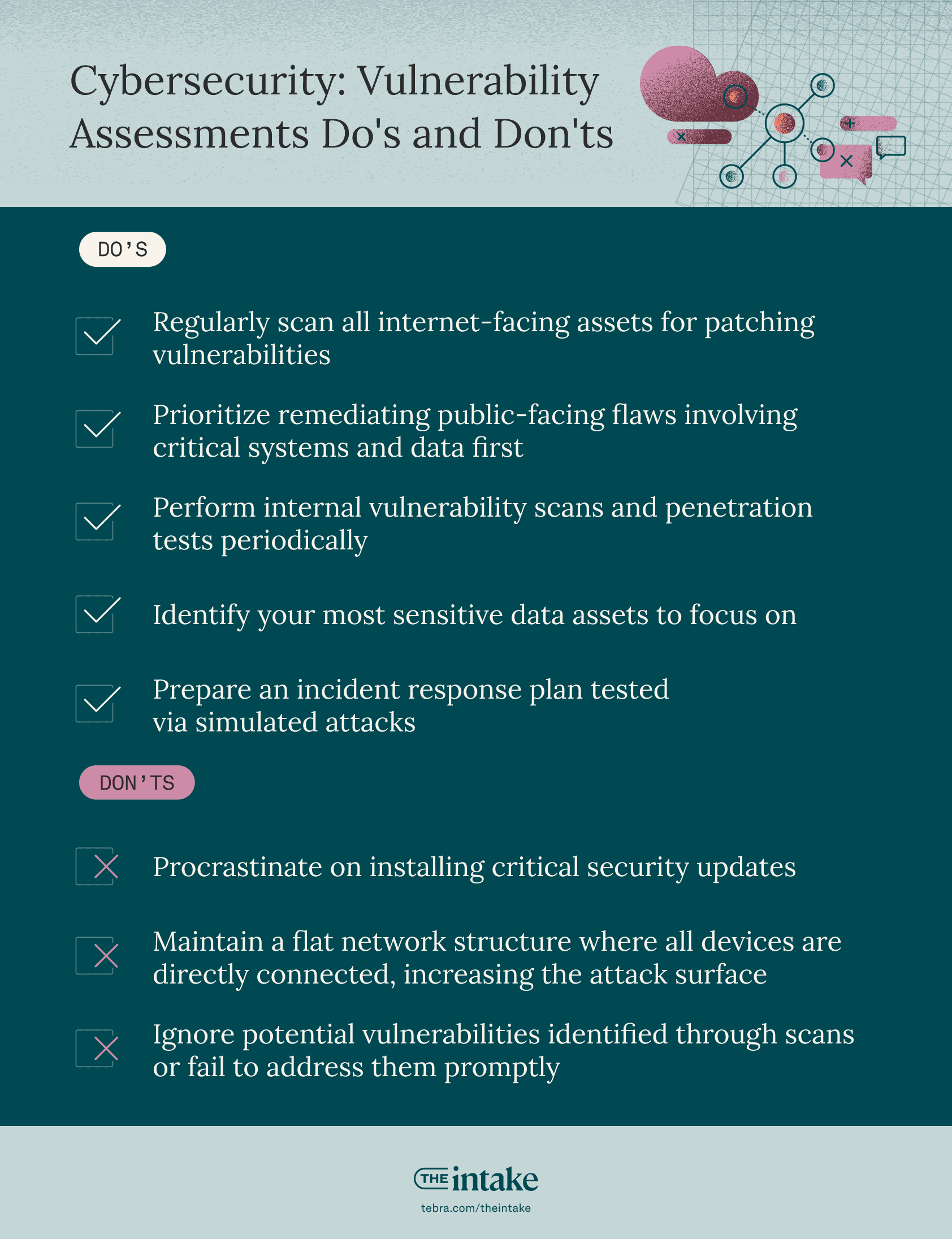
| Vulnerability assessments: Dos | Vulnerability assessments: Don'ts |
| Regularly scan all internet-facing assets for patching vulnerabilities. | Procrastinate on installing critical security updates. |
| Prioritize remediating public-facing flaws involving critical systems and data first. | Maintain a flat network structure where all devices are directly connected, increasing the attack surface. |
| Perform internal vulnerability scans and penetration tests periodically. | Ignore potential vulnerabilities identified through scans or fail to address them promptly. |
| Identify your most sensitive data assets to focus on. | |
| Prepare an incident response plan tested via simulated attacks. |
| Monitoring and backups: Dos | Monitoring and backups: Don'ts |
| Monitor network activity. Be vigilant for suspicious activity that may indicate a potential attack. | Leave patient data unencrypted and therefore vulnerable to breaches. |
| Enforce endpoint protection (EDR) and update all software and OS patches. | Fail to maintain regular backups or test their viability for recovery. |
| Implement data backups with tested restore procedures. | Operate without a plan, leading to confusion and delays during an actual security incident. |
| Perform a security review for each vendor. Understand how a vendor handles sensitive data like ePHI, what safeguards they’ve put in place, and how they continuously monitor for threats. | |
| Consider leveraging a VPN for your entire network. This will ensure all of your internet traffic goes through another secure data center that could identify hostile actors before you do. | |
| Consider cyber insurance to protect your organization from the financial risks associated with cyberattacks. | |
| Provide regular security awareness training to staff. Include cybersecurity best practices like identifying phishing attempts and password hygiene. | |
| Identify and maintain contact information for key personnel. Including IT security staff, legal counsel, and law enforcement. |

Remember: cybersecurity is an ongoing process. Regularly review and update your security measures to stay ahead of evolving threats. Secure vendors like Tebra will provide many of these safeguards for healthcare organizations such as encryption and backups.
Implementing this cyberattack prevention checklist will mean that healthcare providers can significantly bolster their cybersecurity posture. However, even with the most comprehensive preventative measures, no system is entirely foolproof.
Therefore, having a crisis management plan in place is essential to effectively respond to and recover from a potential cyberattack.
“Implementing this cyberattack prevention checklist will mean that healthcare providers can significantly bolster their cybersecurity posture.”
Which cyber risk framework is specific for healthcare?
A cybersecurity framework bridges the communication gap between security leaders.
By applying the same set of standards, healthcare providers can effectively compare the security practices of any vendor they might collaborate with.
With a framework in place that follows common cybersecurity standards, it becomes much easier to define the processes and procedures that your practice must take to assess, monitor, and mitigate cybersecurity risk.
There are 6 common US healthcare-specific cyber risk frameworks:
It’s worth noting that the HIPAA privacy and security rules are not actually cybersecurity frameworks. They outline the absolute minimum security standards for HIPAA compliance.
Best cybersecurity strategies for medical practices
As best practices, healthcare practices should:
Consider implementing multi-factor authentication solutions. These should include phishing-resistant multi-factor authentication where appropriate.
Robust authentication serves as the first line of defense against malicious intrusions and attacks, yet a recent analysis of cyber breaches reported that 86% of attacks to access an organization’s internet-facing systems (such as web and email servers) used stolen or compromised credentials.
Have effective cybersecurity strategies that require mobilization and coordination of resources across public and private stakeholders. These can include hospitals, IT vendors, connected medical device manufacturers, and governments. Mobilizing and coordinating resources across these stakeholders can help mitigate the risks and minimize the impacts of a cyberattack.
Require vendors to demonstrate strong security measures. These can include encryption, strict access controls, comprehensive backup and disaster recovery processes, secure transmission protocols, advanced endpoint protection, and mandatory security awareness training for all personnel.
“By contractually obligating vendors to adhere to these security essentials and provide proof of independent validation, practices can offload much of the cybersecurity burden.”
"By contractually obligating vendors to adhere to these security essentials and provide proof of independent validation, practices can offload much of the cybersecurity burden," says Jesse Salmon, Manager of Information Security at Tebra.
Set up your network and machines from a centralized control point. This can make maintaining a vigilant posture easier. Many IT professionals who work with small businesses manage their IT infrastructure with automation tools. Check to see if your vendor uses such tools and can provide you with reports on a periodic basis. It’s helpful to see the most recent versions of various software programs running in your ecosystem and which versions you’re currently on.
Cybersecurity in healthcare: How to address cyberattacks
Let’s turn to actionable strategies to handle cyberattacks in healthcare practices.
We’ll look at both how to create an incident response plan (IRP) and a crisis management plan. An IRP and the crisis management plan work collaboratively to address a cyberattack.
Incident response plan
Imagine a hospital's network is compromised by a ransomware attack that encrypts critical patient data.
The IRP acts as the hospital's IT security team responding to the malware attack.
There are 6 phases in the incident response process:
1. Preparation: Lay the groundwork for effective response
- Outline roles, responsibilities, communication protocols, and procedures for handling security incidents. This might be the IT security team, incident commander, or public relations personnel.
- Conduct regular training sessions to educate staff on identifying and reporting suspicious activity.
- Maintain and update security tools like firewalls, intrusion detection systems, and anti-malware software.
- Establish clear communication channels for internal and external stakeholders during an incident.
2. Identification: Detect and analyze potential security breaches
- Regularly monitor IDS/IPS logs for suspicious activity like unauthorized access attempts or unusual network traffic.
- Employ endpoint protection software to detect and quarantine malware on individual devices.
- Introduce a system for staff to easily report suspicious activity, such as a hotline or specific email address.
- Train staff to understand the importance of reporting even seemingly minor incidents.
- The IT security team should investigate reported incidents and analyze security tool logs to identify potential malware infections.
- This analysis should determine the nature and scope of the potential breach — such as the type of malware, affected systems, and data compromised.
3. Containment: Stop the attack and prevent further damage
- Isolate infected systems — immediately disconnect compromised devices from the network to prevent the malware from spreading to other systems.
- Disable compromised accounts by revoking access to any accounts potentially compromised by the malware.
- Implement well-defined, pre-approved processes for actions such as:
- Safely restoring from isolated backups to recover operations.
- Resetting compromised credentials and user accounts.
- Engaging incident response partners/forensics firms if needed.
4. Eradication: Eliminate the threat from the infected systems
- Employ specialized security software and procedures to remove the malware from infected systems.
- Identify and address the vulnerabilities that allowed the malware to infiltrate the system. This may involve installing security patches or updating software.
- Conduct a forensic investigation to determine the root cause of the attack and identify any additional compromised systems or data.
5. Recovery: Restore affected systems and data
- If possible, restore data from backups that haven't been compromised by the malware.
- In situations where data recovery is not possible, the affected systems may need to be rebuilt from scratch.
- Ensure all restored or rebuilt systems function correctly and are free of malware before reconnecting them to the network.
6. Lessons learned: Improve future preparedness
- Conduct a post-incident review to analyze the incident response and identify weaknesses in security posture and response procedures.
- Revise the IRP to address identified gaps and improve future response effectiveness.
- Share the findings from the incident review with partner healthcare organizations to enhance overall cybersecurity awareness and preparedness.
The ultimate goal is to contain the immediate threat (ransomware attack), recover critical data, and minimize the long-term consequences (loss of patient trust, legal issues).
Each phase of the IRP is critical, and it is important everyone knows which phase is current. As threats can change quickly, it is vital to focus on the most important task.
Incident response best practices
For the best cybersecurity in healthcare practices, it is crucial to refer to and follow the documented incident response or crisis management plan immediately.
"The biggest mistake one can make is being unprepared and having to make up the response on the fly," Salmon notes. "Such unpreparedness can result in missteps, compliance lapses, and potentially greater impacts."
“Each phase of the IRP is critical, and it is important everyone knows which phase is current.”
By incorporating lessons learned from cyber incidents and following industry best practices, you can continuously strengthen your overall security posture, enhance your incident response capabilities, and better protect your organization against evolving cyber threats.
Creating a crisis management plan
Building upon the foundation of the IRP, let's explore how to create a comprehensive crisis management plan to address the broader consequences of a cyberattack in a healthcare setting.
Here's a breakdown of the key steps involved:
1. Assemble a crisis management team
Establish a dedicated team of individuals from various departments, including IT security, public relations, legal counsel, and senior management. It’s essential to clearly define roles and responsibilities for each team member.
2. Develop a communication strategy
Pre-determine communication channels for internal and external stakeholders. Internally, ensure staff are informed about the situation, potential consequences, and recommended actions. Externally, establish protocols for communicating with patients, media outlets, and regulatory bodies.
3. Prepare crisis communication materials
Develop pre-approved communication templates and statements to ensure consistent and factual messaging during a crisis. Identify a designated spokesperson to deliver official information to the public.
4. Conduct training and drills
Regularly train the crisis management team on their roles, communication protocols, and media relations best practices.
To test the effectiveness of the crisis management plan and identify areas for improvement, simulate potential cyberattack scenarios through tabletop exercises.
5. Legal and regulatory considerations
Consult with legal counsel to understand reporting requirements and potential legal ramifications associated with a data breach.
“Familiarize yourself with relevant data privacy regulations (such as HIPAA) and establish procedures for complying with reporting mandates in case of a cyberattack.”
Familiarize yourself with relevant data privacy regulations (such as HIPAA) and establish procedures for complying with reporting mandates in case of a cyberattack.
6. Maintain and update the plan
Regularly review and update the crisis management plan to reflect changes in the regulatory landscape, evolving cyber threats, and lessons learned from past incidents. Part of this phase includes analyzing the root cause, identifying gaps, and updating defenses and staff training accordingly.
By following these steps and working in close collaboration with the established IRP, healthcare organizations can effectively manage the broader consequences of a cyberattack.
This includes mitigating reputational damage, ensuring patient trust, and navigating any legal or regulatory hurdles that may arise. A well-defined crisis management plan serves as a critical roadmap for guidance through a complex and potentially damaging situation.
Staying informed on cyberattacks
One of the most effective ways to enhance your organization's cybersecurity is to learn from real-world cyber incidents and incorporate those lessons into your security measures.
While details of high-profile breaches may be limited, there are reputable sources that can provide valuable insights and best practices, such as:
- CISA (US Cybersecurity & Infrastructure Security Agency): They offer valuable information on cyber threats and security.
- H-ISAC (Health Information Sharing and Analysis Center): This group focuses specifically on healthcare industry threats.
The Office for Civil Rights (OCR) and the Office of the National Coordinator for Health Information Technology (ONC) at the US Department of Health and Human Services (HHS) have released version 3.4 of the Security Risk Assessment (SRA) Tool.
Conducting a yearly security risk assessment is required to be compliant with HIPAA, so this tool is designed to aid small and medium-sized healthcare organizations in their efforts to assess security risks.
“Businesses should conduct a risk assessment at least annually, but given the pace at which new threats are emerging, businesses would benefit from a semi-annual or possibly quarterly review process.”
"Businesses should conduct a risk assessment at least annually, but given the pace at which new threats are emerging, businesses would benefit from a semi-annual or possibly quarterly review process," says Anthony Comfort, VP of Product Management at Tebra. Comfort says that one way to make this more achievable is by separating checklist items into those that can be reviewed annually vs. items that should be reviewed more frequently. "For example, checking your systems for needed updates should be a frequent activity, but security and awareness training for employees may be something you do yearly," he adds.
Use endpoint detection and response tools for added security
In addition, consider using endpoint detection and response (EDR) tools for an extra layer of security.
Here's why EDR is helpful:
- Constantly monitors your devices: It keeps a close eye on everything happening on your computers.
- Smarter than regular antivirus: Uses advanced techniques to spot even new and unknown threats.
- Gathers evidence: Helps you understand what happened during an attack.
- Real-time response: Allows you to take action against threats quickly.
- Always learning: Stays updated with the latest information to stay ahead of attackers.
Tebra is dedicated to helping doctors build an industry-leading security program to ensure all patient data is safe and protected. To ensure a top level of security, Tebra implements the best practice security frameworks, using both in-house and third-party tools and services.
You might also be interested in
Optimize your independent practice for growth. Get actionable strategies to create a superior patient experience, retain patients, and support your staff while growing your medical practice sustainably and profitably.